Understanding the Process of Auditing Smart Contracts: Workflow,Best Practices and Techniques
End-to-End Guide
What is a Smart Contract Audit?
A smart contract audit is a process of reviewing the code of a smart contract to identify potential vulnerabilities and security risks. The goal of an audit is to ensure that the smart contract is secure and free from errors before it is deployed on the blockchain.
The audits usually follow a four-step procedure:
Initial Analysis: Smart contracts are provided to the audit team for initial analysis. This involves reviewing the code and identifying potential vulnerabilities and security risks. This step is crucial as it sets the foundation for the rest of the audit process and helps identify any issues that need to be addressed before deployment.
Findings Presentation: The audit team presents their findings to the project for them to act upon. This helps the project team understand the issues found and take necessary action. This step is important as it allows the project team to make informed decisions about how to address any issues found.
Changes Implementation: The project team makes changes based on the issues found. This helps to address any vulnerabilities or security risks identified in the initial analysis. This step is necessary to ensure that the smart contract is secure before deployment.
Final Report: The audit team releases their final report, considering any new changes or outstanding errors. This report serves as a comprehensive document that highlights the issues found, the changes made, and the overall security of the smart contract. This step is important as it provides transparency and accountability for the smart contract and its security.
Why is Smart Contract Auditing Important?
Smart contracts are self-executing contracts with the terms of the agreement written directly into code. They are immutable and automatically execute when certain conditions are met. As they are used to handle valuable assets, it is crucial to ensure that they are secure and free from errors. Smart contract auditing can help identify and fix vulnerabilities before they can be exploited by malicious actors. Smart contract audits can also help to ensure that the smart contract is functioning as intended and that it is compliant with any relevant regulations.
Smart Contract Auditing Workflow
Code Review: Review the smart contract code manually to identify any potential vulnerabilities or security risks. This step is important as it allows the audit team to understand how the code works and identify any potential issues.
Automated Scanning: Use automated tools like Mythril, Oyente, and Securify to scan the code and identify potential vulnerabilities. This step is important as it allows the audit team to quickly identify any potential issues that may not be obvious during a manual code review.
Test Execution: Test the smart contract on a test blockchain network to identify any issues that may not have been identified in the code review or automated scanning. This step is important as it allows the audit team to identify any issues that may only appear when the contract is executed on a live blockchain network.
Remediation: Address any issues identified in the previous steps by making changes to the smart contract code. This step is necessary to ensure that the smart contract is secure before deployment.
Final Review: Re-review the smart contract code and re-test it to ensure that all issues have been resolved. This step is important as it allows the audit team to ensure that all issues have been addressed and that the smart contract is secure before deployment.
Top 5 most common smart contract vulnerabilities:
Re-entrancy: A type of attack that exploits a vulnerability in smart contract code that allows an attacker to repeatedly call a function before the initial call is completed.
Overflow/underflow: This occurs when a smart contract does not properly check for integer overflow or underflow, which can lead to unexpected behaviour and potentially allow an attacker to access or manipulate sensitive data.
Unchecked return values: This occurs when a smart contract does not properly check the return values of external function calls, which can lead to unexpected behaviour and potentially allow an attacker to access or manipulate sensitive data.
Insufficient access controls: This occurs when a smart contract does not properly implement access controls, which can allow unauthorized users to access or manipulate sensitive data.
Unchecked user inputs: This occurs when a smart contract does not properly validate user inputs, which can allow an attacker to inject malicious data and potentially access or manipulate sensitive data
Example of Re-entrancy:
In this example, the withdraw () function allows a user to withdraw a specified amount of funds from their balance. However, the function also calls an external contract (attacker) with the same amount of funds before updating the user's balance. If the external contract is controlled by an attacker, they can repeatedly call the withdraw () function before the user's balance is updated, allowing them to drain funds from the contract.
Vulnerable Code:
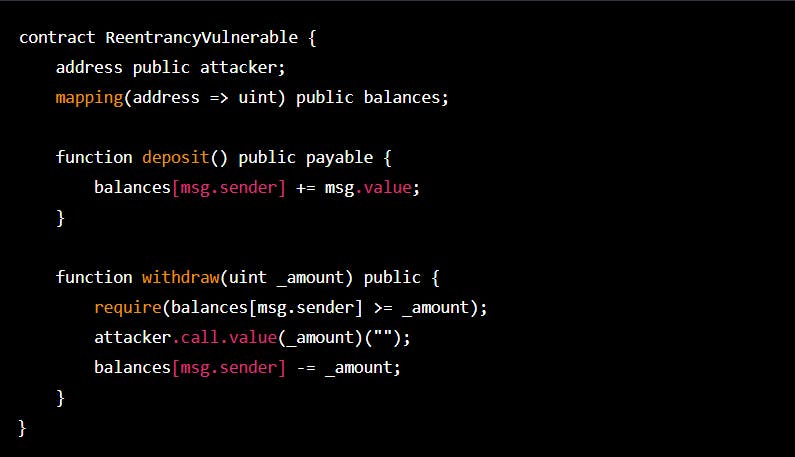
Audited and Improved Code:
To prevent this vulnerability, a guard condition can be added to the contract like this:
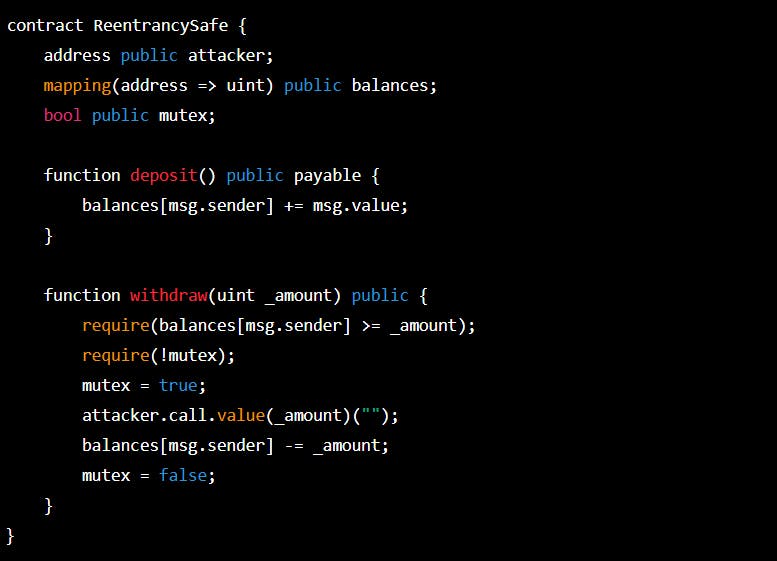
In this example, a Boolean variable mutex is added to the contract and is set to true before calling the external contract and set to false after updating the user's balance. This prevents the withdraw () function from being called
multiple times before the user's balance is updated, effectively blocking the re- entrancy attack.
It is important to note that, this is just an example and there are various other ways to prevent re-entrancy attacks this should be implemented with care as every smart contract is different and has different requirements.
General best practices for smart contract auditing :
• Thoroughly reviewing the code and understanding how it works before conducting the audit.
• Using automated tools to scan the code and identify potential vulnerabilities. • Testing the contract on a test blockchain network to identify any issues that may not have been identified in the code review or automated scanning.
• Addressing any issues identified during the audit by making changes to the smart contract code.
• Re-reviewing and re-testing the code to ensure that all issues have been resolved before deployment.
• Keeping the code and libraries up to date and using audited and tested libraries. • Having proper access control and authorization mechanisms in place to prevent unauthorized access.
• Handling sensitive data such as private keys securely.
• Having event logging and monitoring mechanisms in place to track and monitor any actions taken on the contract.
Summary:
A smart contract audit is a process of reviewing the code of a smart contract for security vulnerabilities and bugs before deployment on the blockchain. The audit process includes initial analysis, presentation of findings, implementation of changes, and a final report. It is important to conduct smart contract audits to ensure the security and proper functioning of the contract. The audit workflow includes code review, automated scanning, testing, and remediation. Best practices include checking for common vulnerabilities, proper use of libraries, access control and data handling, and event logging.
